Combating Caller ID Spoofing on Mobile Phones
What's NEW?
Oct 31, 2018: CEIVE received Best Demo Award at MobiCom’18. Congrats to Haotian!
Oct 2, 2018: CEIVE is On the Media inverse.com.
Oct 1, 2018: CEIVE demo combating “Consulate Phone Scam” is at Youtube.com.
Problem
Caller ID spoofing forges the authentic caller identity, thus making the call appear to originate from another user. This seemingly simple attack technique has been used in the growing telephony frauds and scam calls, resulting in substantial monetary loss and victim complaints. Unfortunately, caller ID spoofing is easy to launch, yet hard to defend; no effective and practical defense solutions are in place to date. We aim to develop callee-only or other practical and effective solution to help mobile users combat caller ID Spoofing.
CEIVE: Combating Caller ID Spoofing on 4G Mobile Phones Via Callee-Only Inference and Verification
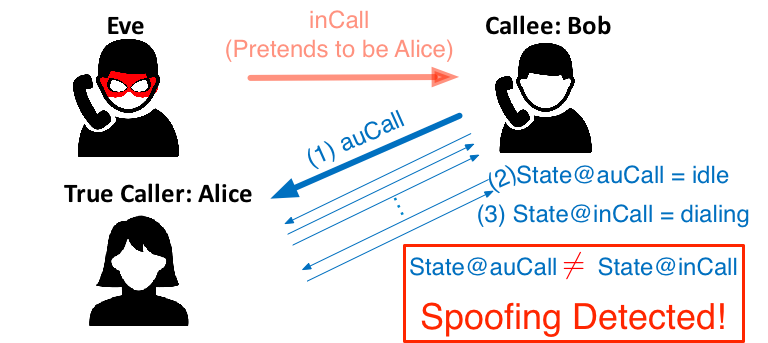 |
CEIVE (Callee-only inference and verification) is an effective and practical defense against caller ID spoofing. It is a victim callee only solution without requiring additional infrastructure support or changes on telephony systems. We formulate the design as an inference and verification problem. Given an incoming call, CEIVE leverages a callback session and its associated call signaling observed at the phone to infer the call state of the other party. It further compares with the anticipated call state, thus quickly verifying whether the incoming call comes from the originating number. We exploit the standardized call signaling messages to extract useful features, and devise call-specific verification and learning to handle diversity and extensibility. We implement CEIVE on rooted Android phones and test it with all top four US mobile carriers, one landline and two small carriers. It shows 100% accuracy in almost all tested spoofing scenarios except one special, targeted attack case. |
Watch our CEIVE demo against “Consulate Phone Scam”
 |
Scam calls from Chinese consulate have been repeatedly report in recent news and alerts (e.g., FTC, China-embassy, FCC, NBC, Washington Post, CBS, NPR, WNYC, XinhuaNet ). One victim in San Francisco even lost $3M ([https:goo.gl/pJYFNM SFgate).
Here is our CEIVE demo which successfully detects this spoofing (Done on August 15, 2018).
Watch our 1-min Video for MobiCom’18
Publications
CEIVE: Combating Caller ID Spoofing on 4G Mobile Phones Via Callee-Only Inference and Verification
Haotian Deng, Weicheng Wang, and Chunyi Peng, MobiCom’18Demo: Combating Caller ID Spoofing on 4G Phones Via CEIVE
Haotian Deng and Chunyi Peng, MobiCom’18 (Best Demo Award)
<div class=“small”> <!– Start of StatCounter Code –> <!– Start of StatCounter Code for Default Guide –> <script type=“textjavascript”> var sc_project=7634877; var sc_invisible=0; var sc_security=“626600d3”; <script> <script type=“textjavascript” src=“http:www.statcounter.comcountercounter.js”><script> <noscript><div class=“statcounter”><a title=“jooml visitors” href=“http:statcounter.comjoomla” target=“_blank”><img class=“statcounter” src=“http:c.statcounter.com76348770626600d30” alt=“joomla visitors”><a><div> <noscript> <br> <!– End of StatCounter Code for Default Guide –> <div>
