Overview of Wireless Architectures and Products
What is Wireless Communication?
Anyone who is up to date on the Wireless World will reassuringly say that the dependency on Wireless Technology has increased over the last year. These days, any person from the age of 5 to 95 can hold some sort of portable device – be it a cell phone or a pager or a toaster – that not only allows one to communicate with family and friends, but now one can check his email, his stock portfolios, and browse the web all from whatever device he is holding in his hand or nearby on his desk – it could even be a toaster (Audrey anyone?)[1]
Perhaps as little as four years ago no one would have ever thought that the technological world – which literally exists worldwide and not only in the heart of the Silicon Valley as every one says – could bring our favorite hobbies of web browsing and email to our brand new miniature Nokia cellular phones. The Wireless Hierarchy, to be discussed in the next section, breaks down into several components. The question is no longer “How do we get data to a portable device (such as a cellular phone)?” Now that this technology has been developed and continues to be developed since certainly not everything has the Internet on it (e.g. our shoes), the question becomes “How fast can we get this data to a portable device (such as my toaster)?”
The terms “Wireless” and “
Wireless Communication is simply a medium. Wireless Communication is about the tools used to communicate from one device to another. As subscribers to such technology, one needs to find the best type of wireless services that suits his needs. The goal of this survey paper is not to market any particular product that utilizes wireless technology of any sort. What shall be described in this paper is simply to define and understand Wireless Architecture and discussing the various protocols that exist in this field today. Several products will be mentioned and comparisons will be made, but in no means will a particular product be marketed.
Wireless Application Protocol, also known as WAP to those who inhibit the Wireless World, is a survey paper of its own. However, WAP will be addressed as well not only because there is a need to discuss WAP, but because it would be unjust to not even mention WAP when discussing Wireless Technology. WAP has been one of the most recent and the most fully developed protocols out there. In very little time, WAP served as a basis and model for other protocols such as another very recent protocol on the market today – Ericsson’s Bluetooth. Although these protocols serve different purposes, they cover similar bases and have very similar concepts and goals, which shall also be discussed ahead as well. WAP allows things such as web surfing on cellular phones – something other protocols did not cover. This highlights one of the main topics of this survey paper, all which will be discussed ahead.
Components of Wireless Communication
Although each protocol has different specifications and criteria, there are general characteristics and goals that each protocol tries to achieve. Several of these protocols are discussed in this survey paper as well. Below are some general guidelines these protocols try to follow:
- Unlimited roaming and range: The location of the user with the portable device is irrelevant. No matter how far or how near a user is from the base provider, data can still be sent and received.
- Guarantee of Delivery: All messages and data is guaranteed to be delivered regardless of where a user is located or the user’s status. Even if the portable device is turned off, when it is turned on again, the user will see a new message.
- Dependability of Delivery: All messages are guaranteed of accurate and full transmission.
- Notification: Notifies the user that there is data that has been sent and needs to be looked at.
- Connectivity Options: Send and receiver are given a wide range of options not only in hardware for the portable device, but also are given options in receiving messages (choosing a type of connection for instance).
- Millions of Users: Ability to engage millions of users.
- Priority Alerts: Able to distinguish between messages and data that are of higher importance than others. Able to control high-priority data traffic and do so correctly and rapidly.
- Communication: The ability to communicate between one user to another through one portable device to another where each portable device holds reliable and user-friendly software applications.
- Host Reconfiguration: The ability to reconfigure when changing environments. For example, Person A is carrying a Palm Pilot that uses Bluetooth. Person A enters the office where there is an entire Bluetooth network set-up and Person A’s Palm Pilot configures to the settings of the office network. The end of the day comes, and Person A starts driving home. Person A gets home and walks inside where Person A’s home is set up with an entirely different Bluetooth network. Person A brings the Palm Pilot out and the Palm Pilot automatically reconfigures itself to the settings of the Bluetooth network in Person A’s home. Therefore, whether the Palm Pilot works in one environment and can detect when it has been moved to another environment and can set itself up wherever it is located.
- Host Mobility: One host contains its settings on a network – its IP address, Subnet Mask, Gateway Address, and so on. Now this one host decides to move somewhere else, this means that the host will have to change its settings all over again, but has to let others know that it has moved. Flexible mobility allows the host to come and go as it pleases and not even needing to alert others of its move. Communication with the host is still possible even if it has moved.
- Dynamic Encapsulation: The need to register a mobile host with its base agent, perhaps using a login and logout request and alerts of activation and inactivation. This will prevent forged logins and having one’s precious date to be re-routed somewhere it should not be.
As mentioned before, different protocols serve different needs and offer different services. Outlined above are general things that most protocols that support the Wireless World might already offer or are looking to offer.
Wireless Application
Protocol (WAP)
The Basics Behind WAP
The Wireless Application Protocol has become the standard for communication between server applications and its clients. That is exactly what the Wireless Application Protocol is; for example, WAP is used as a standardized method so that a cellular phone can talk to a server among the cellular network that it belongs to. Because WAP has become so global, it no longer is bounded by the means of the cellular market. WAP has become the link of the Internet to the Mobile World, bridging a gap between two of the top industries of the world.
WAP also follows a model similar to the Internet. The Internet itself has a layered protocol stack. The portable device using WAP has browser software that connects to a WAP Gateway and sends requests to receive data from web servers. Data could be a web page or an email. The content is then sent back to the portable device, and depending on the capability of the portable device to receive and view data, the data is received and viewable.
WAP founders include Ericsson, Nokia, Motorola, and
Phone.Com (formerly Unwired Planet). In
December 1997, these three large companies, all with strong influence on the
Basic specifications of WAP include: micro browsing, scripting, wireless telephone applications, and a layered protocol stack to be discussed in the next section.
Some Quick Technical Issues
Before beginning a description about the WAP Stack, the user should be briefed on a slight technical introduction. WAP is the connection between the Internet and the Wireless World, and there are two things that need to be addressed:
- HTML vs. HDML vs. WML: Hyper Text Markup Language (HTML) is the language that is used to translate data to a web browser to be viewed by a user. Handheld Device Markup Language (HDML) is used to incorporate handheld or portable device applications such as a micro browser. Wireless Markup Language (WML) is a language derived from HTML that is used with WAP to incorporate WAP features.
- How to incorporate WAP: Here is an example: We have a user that uses a WAP-compliant mobile phone. That is, his phone has WAP features on it such as a small email application and a mini browser. He decided to view something on his mini browser, thus requesting to see data. The request is passed to the WAP Gateway of his mobile service network, where their servers retrieve the information in standard HTML format or perhaps even in WML if the server can make the translation through a filter in the WAP Gateway. One the request is sent through the WAP Gateway, the WAP Gateway in turn sends the data to the WAP client to view on his micro browser. Diagram goes here.
The WAP Model
WWW Model Diagram: The World Wide Web Model follows a three-layer protocol. Referring to the diagram, the WAP model follows the World Wide Web model in that there is an Origin Server, a Proxy, and a Gateway. The Origin Server serves as the main web server where one would find CGI scripts and other sorts of scripts. The Origin Server also holds content that Clients will want to view. The Proxy serves as an application that connects from the Origin Server to the Gateway. The Proxy sends and receives content to the Gateway. The Gateway is another server that acts as an origin server between the client and the origin server. Most clients would not be able to tell if they are in contact with the Gateway service. The Gateway serves as a protection for the Origin Server. Not all World Wide Web Models have Gateways however; but most do.
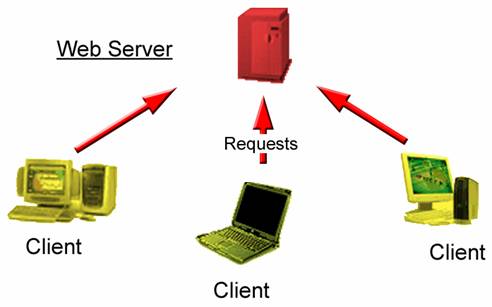
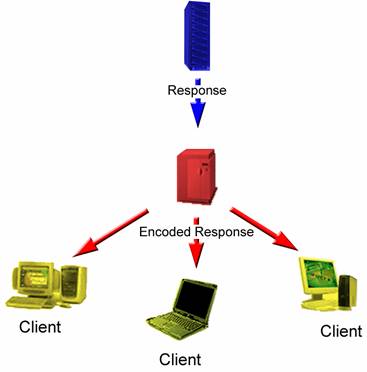
Figure 1a. WWW Model. Clients make requests to the server for data.
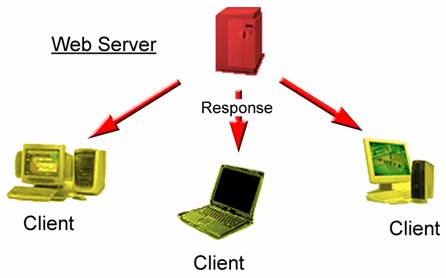
Figure1b. WWW Model. Web Server responding to Client requests and sending requested data.
The WAP Model has a similar set-up as the World Wide Web Model. There is also an Origin Server with a Gateway. Again the Origin Server contains content and scripts, while the Gateway acts as a server to the Clients. The Gateway uses the proxy. In the WAP Model, the Client, for example, could be a mobile phone. The Client makes a request in WML or in HDML depending on the device and request, and the Gateway will encode the request to the Origin Server and once the Origin Server responds with information to send, it sends the data back through the Gateway, where the Gateway will encode the information again, and send it to the Client.
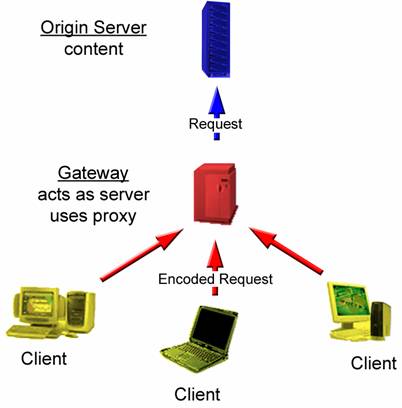
Figure 2a and 2b. The WAP Model follows closely with the WWW Model.
WAP Architecture is divided into several layers. This is often called the ‘WAP Stack’. Below are technical descriptions of each layers.
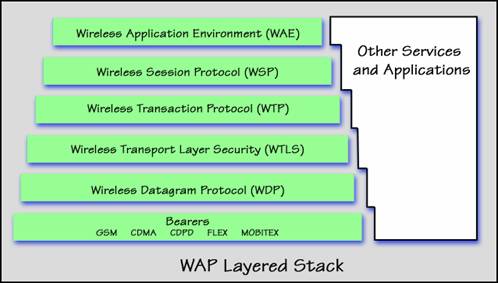
Wireless Application
Environment (WAE)
The goal of WAE is to establish an environment that allows users to build applications that can be used over a wide variety of wireless systems that can be implemented efficiently. WAE is able to be used with Phone.com’s HDML, the World Wide Web’s HTML, and should work with other technologies of the web, such as Uniform Resource Locator (URL) and Hyper Text Transfer Protocols (HTTP), and other modern technologies that are found within a mobile network.
In the WAP model, WAE would be the application environments that sends and receives requests from the Clients to the Gateway to the Origin Server. WAE relies heavily on URL and HTTP ideals by assuming the existence of a gateway server and support from the WAP gateway in the network.
WAE is composed of user agents such as browsers, text editors, date book or phonebook. WAE is also composed of scripting, higher-lever programming languages and image formats. WAE uses languages such as WMLScript (similar to JavaScript) and WML (similar to HTML).
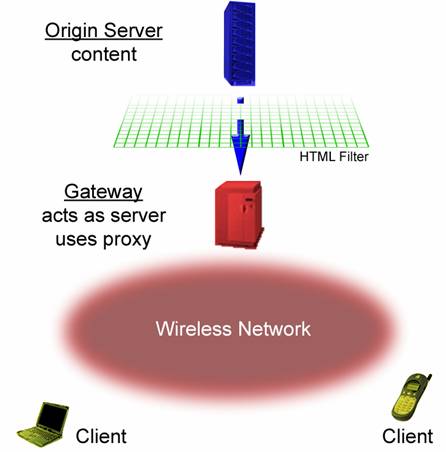
Figure 3. Basic Wireless Network.
Wireless Session Protocol (WSP)
The Wireless Session Protocol is the layer that deals with communication between client and proxy or server. The WSP provides dialog between client and server. WSP provides the following services:
- Opens a session of communication between client and server.
- Establishes a protocol and negotiation between client and server.
- Exchanges encoded data between client and server.
- Exchanges request and replies between client and server.
- Supports several asynchronous transmission of data.
Wireless Transaction Protocol (WTP)
The Wireless Transaction Protocol, in a simple definition, deals with the transaction of data. WTP handles transactions, re-transmission of data, and with the separation and concatenation of data.
This particular protocol has a separate interface that manages and referees the WTP layer and the settings of the handheld device. This management application is known as the WTP Management Entity. For WTP to work, the following factors are important:
1. The handheld device is within coverage area of base agent.
2. The handheld device is turned on and has a power and is reliable.
3. Resources are adequate especially with the CPU and memory.
4. WTP settings are correctly inputted.
The WTP Management Entity makes sure the above factors are valid during the transaction session. Of course, it is assumed that the user wants to receive and transmit data.
Wireless Transport Layer
Security (WTLS)
The Wireless Transport Layer Security is the layer that handles security of data and validity of data between two communicating to manage, start, and finish security issues between two portable devices.
To transport data, WTLS needs: the source address and port number to identify the message creator, and from where the message is being sent, the destination address and port number to which data is being sent, and of course, the data itself. WTLS has a connection interface which provides a connection protocol between client and server.
Wireless Data Protocol (WDP)
The Wireless Data Protocol acts as the communication layer between the upper level protocols (WTLS, WTP, and WSP), and the bearer services. WDP allows the upper layers to function independently from the wireless network at hand, as long as the WTP layer is specifically set to the settings of the bearer settings.
The function of the WDP is to provide a stable environment so that any of the underlying bearers can operate using WAP. WDP can be adapted to different bearers with different services however the services offered by WDP remains constant thus providing a continuous interface to the upper layers of the WAP stack.
Bearers
The bearers of WAP are the products or other types of medium that implements WAP in their network and in their technology, such as CDPD, Mobitex, and GSM.
Technical Challenges of WAP
Of course every great protocol or specification out there for wireless technology will definitely have its drawbacks. With WAP, there are several problems that may or may never get addressed during its development:
- Since WAP is designed for portable devices, important details matter: such as dealing with small screen sizes (a Palm Pilot or mobile phone). A small screen size does not allow high resolution or high pixel images to be seen clearly.
- Because WAP is designed for portable devices, there is limited device memory so that not a lot of data can be stored.
- WAP allows two devices to communicate only, and data transfers are usually done with Infrared, therefore the devices have limited range of data transfer.
- WAP also works on devices that have limited bandwidth.
- There are no “cookies” available to hold the session together.
Bluetooth
What is Bluetooth?
Those who are not so savvy in the technology and wireless worlds may or may not know
what not Bluetooth is. The word 'Bluetooth' tends to be placed in the same sentence with the words 'WAP' and 'Wireless'. According to the Bluetooth website, a frequently asked question is: is Bluetooth a protocol, a standard, a technology, or an actual product?
A quick answer to this question is: Bluetooth is not an actual product. Bluetooth is a standard for wireless communication between short-ranged radio links to PCs to mobile phones.
The Special Interest Group, also known as its acronym SIG, includes companies such as: 3Com, Ericsson, IBM, Intel, Lucent, Microsoft, Motorola, Nokia and Toshiba, among the few big companies. SIG contains many members of smaller companies as well.
The Technology Behind Bluetooth
Global Band
For Bluetooth to work globally, the frequency band must be established and available universally. Bluetooth only uses one frequency band that is available worldwide, and this is the ISM (Industrial-Scientific-Medical) because it runs at the appropriate frequency required for Bluetooth and in fact, ISM is the only band on the market that runs to this necessary frequency.
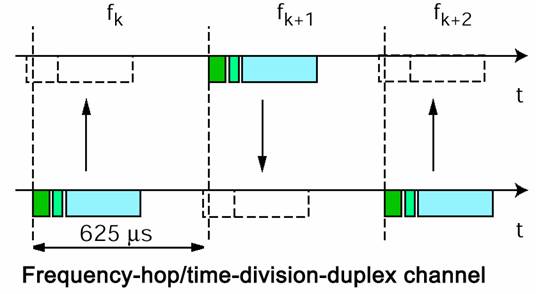
Frequency Hopping
When working with Bluetooth, one must realize that the connections of Bluetooth are primarily dependant on frequency since its short-ranged communication take into consideration interferring signals: such as garage door openers, walkie-talkies, microwaves, toaster ovens, and so on. Bluetooth takes care of this by hopping to different channels depending on where the Bluetooth device is located.
Figure 4. Packet data in op-code format. Taken from “BlueTooth – The Universal Radio Interface for ad hoc, wireless connectivity” by Jaap Haartsen (March 1998).
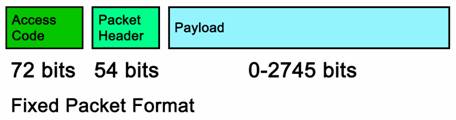
The standard of frequency hopping is easy to use and understand and thus implemented by Bluetooth. Frequency hopping divides the frequency band into different channels that are “hopable” – meaning that the frequency will hop from one channel to the other, depending where the Bluetooth portable product is located. When there is some sort of interference – for example, maybe a garage opener – then the channel “hops” to another channel so that transmission and receiving of data is still easy to do. However interference handling is not always guaranteed and there are times when an interference will jam the entire Bluetooth device’s connection. This is where error handling comes in and takes care of such problems by restoring some error bits.
Figure 5. Frequency Hopping diagrammed on f-t axis (frequency versus time). Taken from “BlueTooth – The Universal Radio Interface for ad hoc, wireless connectivity” by Jaap Haartsen (March 1998).
Although there exist many other standards and protocols to discuss, only few selected and important protocols are discussed in the next sections.
MOBITEX
Background
MOBITEX has become a modern
global standard. Originally developed by
a telecommunications based in
MOBITEX has mostly been developed
through
In 1989, MOBITEX started being
developed by RAM Mobile Data, which since then has become a part of BellSouth,
a nationwide mobile telecommunications company.
MOBITEX has not become totally worldwide yet, as it is still undergoing
development in several other countries, including
MOBITEX Architecture
MOBITEX technology revolves around the node. A node is a data structure that has the ability to transmit its data to anywhere it is assigned to. In the case of MOBITEX, each node acts as a base where data stops. There are three different types of nodes in MOBITEX technology. One type of node is known as the base station. The base station connects to local switches through the local telephone company. A local switch is the second type of node. The last type of node is the regional switch. The regional switch is where the local switches connect to for access to long distance facilities. At the higher level of all these nodes is the main exchange that connects with other networks and bearers. Above the main exchange is something referred to as the network control center (NCC). The NCC supports network management and facilitates data traffic and such.
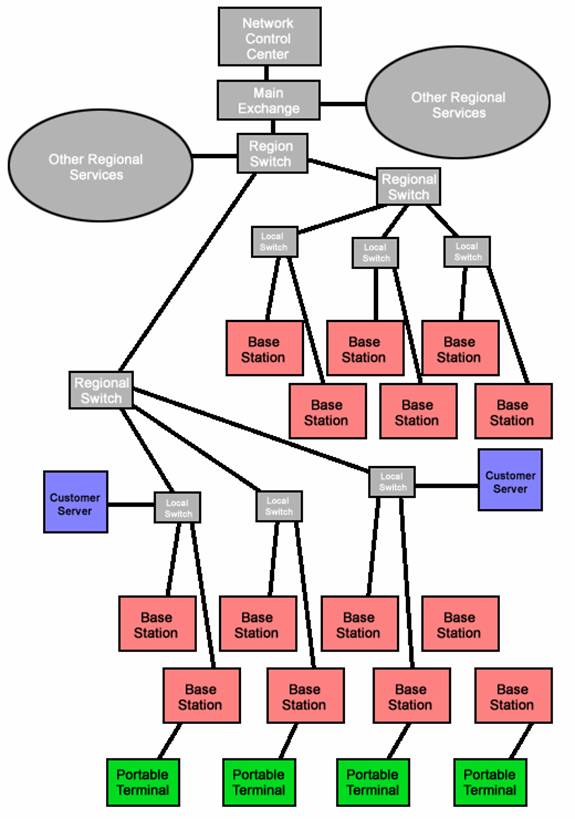
Figure 7. A MOBITEX environment.
MOBITEX Technology
As with any protocol, MOBITEX offers several features:
- Easy roaming so that there is no need to register with base when moving from one area to another.
- Store and forward services that guarantee delivery of a message regardless of user’s location and status.
- Reliability of message being transmitted in full and accurately.
- Able to have millions of users.
- Transfers a variety of messages from data messages to text messages to higher encrypted data messages.
- Handles a priority queue for received and sent messages – able to deliver messages with higher priority than others.
- Network security: login and logout options along with notifications of status (activated/inactivated).
- Retransmit data if there are any errors in first time transmission
- Able to find the right channel and frequency in order to work properly and accordingly.
CDPD
Background
Cellular Digital Packet Data, otherwise CDPD, is a mobile technology that transmits data over the system offered by Advanced Mobile Phone Service (AMPS). CDPD was primarily developed by IBM but its development has now moved to a communal effort among several big companies including Ameritech, AirTouch, and GTE – now Verizon. In the early stages of CDPD development, CDPD offered packet-switching data transmission over analog cellular networks and voice transmission over cellular voice networks.
CDPD devices now take voice channels over an analog cellular network such as AMPS described above. These channels have the ability to transmit relatively short data packets and use these data packets to start a packet-switching session. Like Bluetooth, CDPD uses a channel hopping service among the cellular frequency it uses.
The Wireless Data Forum is an organization that works with the specifications of CDPD and maintains its technology. Unlike other national organizations such as WAP, SIG, or MOA, the Wireless Data Forum not only maintains the specifications of CDPD, but also works on the development of its marketing, provides equipment, and offers technical support. The Wireless Data Forum is aiming to implement CDPD wherever possible.
CDPD Architecture
CDPD works primarily on systems – end
systems (ES’s) and intermediate systems (IS’s). CDPD
Architecture is similar to the model of the World Wide Web. The mobile end system (M-ES) acts as a client
who uses the CDPD network over the wireless environment. The fixed end system (F-ES) acts as a server,
a host, or a gateway depending on the environment. The fixed end system responds to the mobile
end system to give whatever data it has requested.
For the M-ES to be able to communicate with the F-ES, it usually will have a radio modem that attaches to it and manages all the data, data traffic, and other types of protocols that are implemented with the CDPD Architecture.
There are also the intermediate systems (IS’s) which works within the network. There are two types of IS’s: the simple IS that acts as an IP hub or router and has no interest in the network it resides in. The other type of intermediate system is the mobile data intermediate system (MD-IS) which works based on the information it has about the environmental network that it lives in. MD-IS will take care of switching, logins and logouts, status, encryption, and mobility for the device using CDPD.
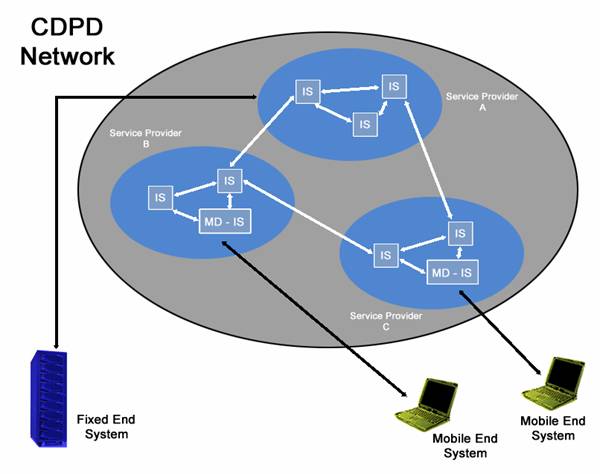
Figure 6. A CDPD Network.
I-Mode
Ii-Mode is the wireless technology produced by the Japanese-based company NTT DoCoMo. I-Mode simply allows cellular phone users to use the Internet on their cellular phones. This technology has just expanded to the European market and is looking to expand and implement WAP in the near future.
I-Mode uses CHTML (Compact Hyper
Text Markup Language) and is a twenty-four hour connection service. There is no dial-up services or external
phone number to dial to. Once the
cellular phone is turned on, the user is connected to the Internet. Email is instant and large files will be easy
to store. The user is billed by how much
data they transmit and receive, not how many minutes they use the
Internet. The cost is added to the
bill. I-Mode has not been launched in
the
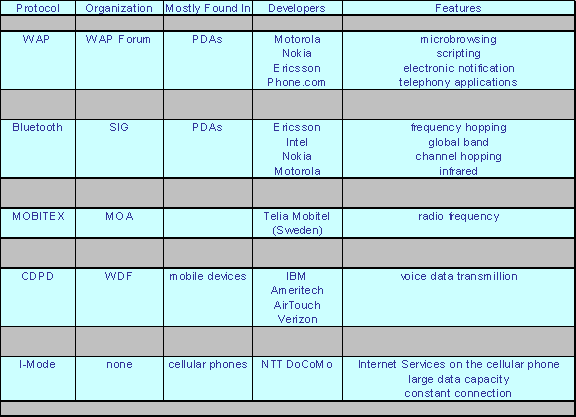
Table A. Protocols discussed in this survey paper.
Concluding Remarks
Wireless devices used to be used only through big companies and large institutes or organizations with certain needs. Perhaps the United Parcel Service (UPS) needs some sort of wireless device or PDA to communicate with the delivery base to confirm a delivery. It is true that these days the UPS man carries email with pagers and a keyboard in order to communicate with its headquarters. The need for wireless technology has grown tremendously in the last two years. Not only has the need for wireless technologies grown vastly – and the industry of wireless technology itself has had a birth – and in some cases a rebirth – and now has become a business of its own.
Wireless technology brings together the two biggest
industries together: the Internet with the
Although these technologies offer many different features and have the capability to behave in many different ways, many of them are compatible with others more than they are competitive (as outlined in table A).
References
http://www.cosmoc.org/pubs/surveys
http://www.ericsson.com/review
http://www.gsmworld.com/technology/yes2wap.html
http://www.cosmoc.org/pubs/surveys/3q99issue/salkintzis.html
http://www.bluetooth.com/developer/specification/specification.asp