Assignment 3
Due beginning of class Monday, 26 March, 2012
- Exercise 11.1 parts 1, 4
- Exercise 12.2
- Exercise 15.6 part 2 (a, b, c)
Security / Access Control
Questions based on the lecture
by Prof. Bertino.
Consider the System R authorization model. Suppose that Bob is the owner of Table T.
- Consider the following graph showing the grant statements on T for the SELECT privilege executed by Bob and users to whom Bob has delegated the grant authorization:
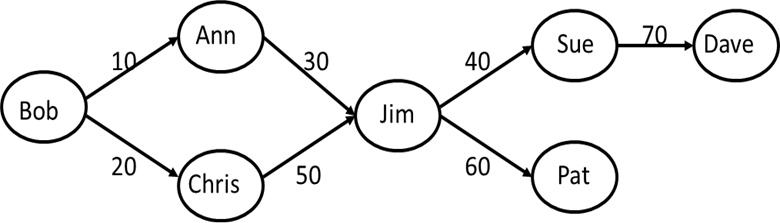
Suppose that Bob at time 100 execute the following revoke operation:
REVOKE SELECT ON T FROM Chris;
- (True/False) After the revoke operation Jim can still read Table T.
- (True/False) After the revoke operation Sue can still read Table T.
- What users can stop Dave from reading T?
-
Consider again Table T owned by Bob and consider the following authorization graph:
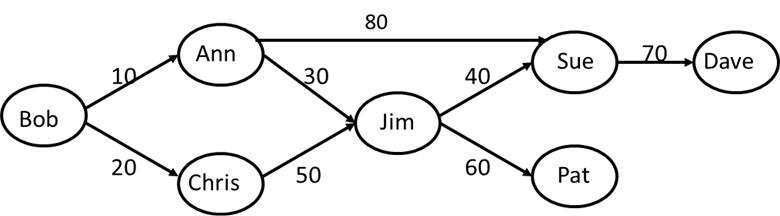
Suppose that the following revoke statements are executed:
Time 100 Ann: REVOKE SELECT ON T FROM Jim;
Time 110 Chris: REVOKE SELECT ON T FROM Jim;
- (True/False) After these revoke operations Sue can still read Table T.
- (True/False) After the revoke operation Dave can still read Table T.
- What users can stop Dave from reading T?
Turning in the assignment
The safest way to turn in the assignment is through
Blackboard; this ensures that we know when
it is turned in, and protects against loss. However, I realize
that some of this is easier to do by hand rather than electronically,
so handing in hard copy at the beginning of the class is acceptable
as well.
This page last modified .