Publications
| Date | Report | Slides |
|---|---|---|
| An Entity-centric Approach for Privacy and Identity Management in Cloud Computing | Paper | Slides |
| Protection of Identity Information in Cloud Computing without Trusted Third Party | Paper | Slides |
| A Trust-based Approach for Secure Data Dissemination in a Mobile Peer-to-Peer Network of AVs | Paper | Slides |
| Protecting PLM Data Throughout Their Lifecycle | Paper | Slides |
| Managed Information Objects for Secure Data Sharing | Proposal | Slides |
Data Dissemination Slides
| Title | Slides (pptx) | Slides (pdf) |
|---|---|---|
| Trusted Router and Collaborative Attacks | Download (pptx) | Download (pdf) |
| Application of Active Bundles | Download (pptx) | Download (pdf) |
Posters
CERIAS Symposium 2015 (best research poster award). PD3: Policy-based Distributed Data Dissemination
Modern distributed systems (such as composite web services, cloud solutions) comprise of a number of hosts, which collaborate, interact and share data. One of the main requirements of these systems is policy-based distributed data dissemination (PD3). In the PD3 problem, the data owner wants to share data with a set of hosts. Each host is only authorized to access a subset of data. Data owner can directly interact only with a subset of hosts and relies on these hosts to disseminate data to other hosts. In order to ensure correct delivery of appropriate data to each host, it is necessary that each host shares entire data even though the hosts are only authorized for certain subset of data. We provide a formal description of the problem and propose a data-centric approach to address PD3. The approach enables policy-based secure data dissemination and protects data throughout their lifecycle. It is independent of trusted third parties, does not require source availability and has the ability to operate in unknown environments. The approach is demonstrated through its application to composite web services.
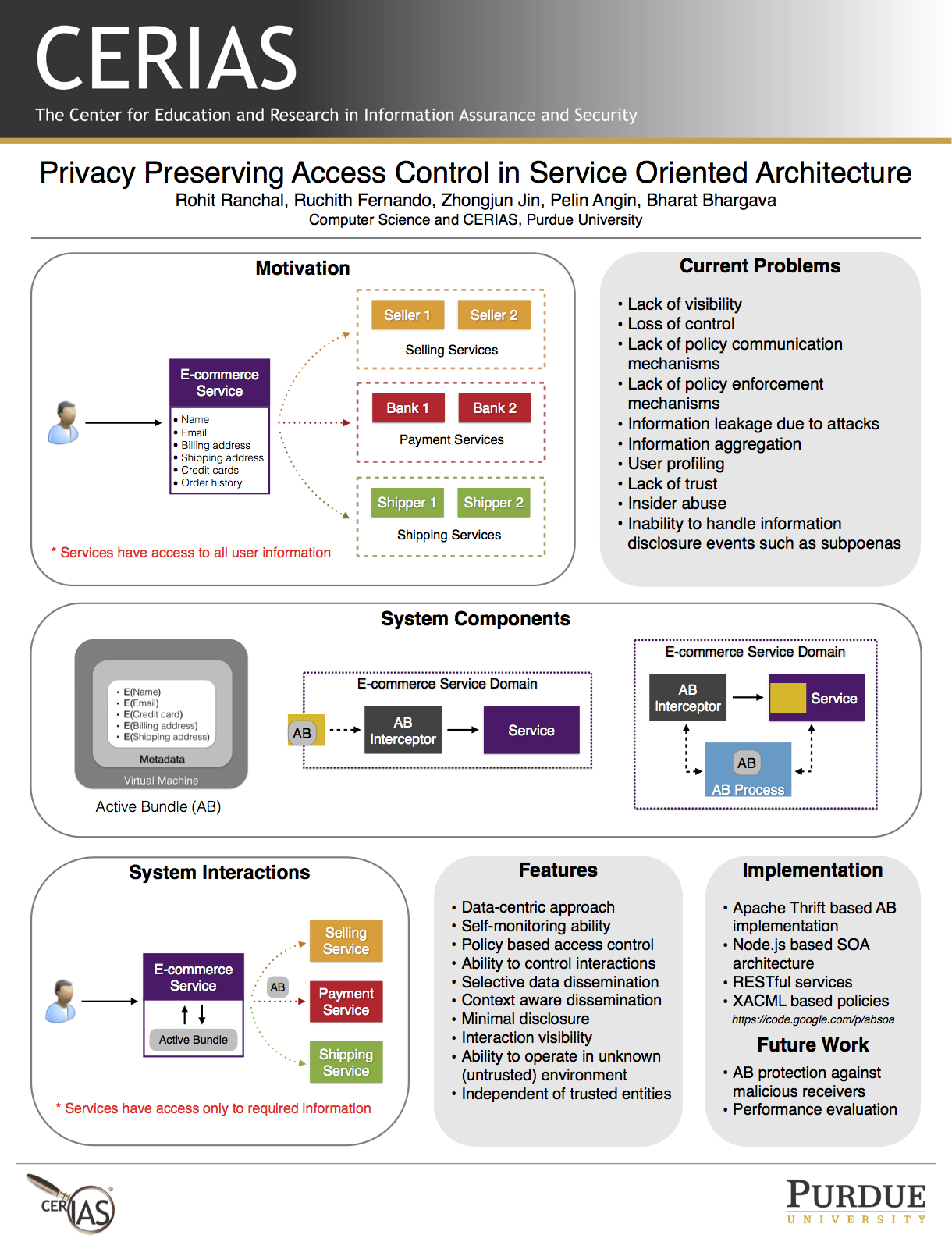
CERIAS Symposium 2014. Privacy Preserving Access Control in Service Oriented Architecture
Service Oriented Architecture (SOA) comprises of a number of loosely-coupled services, which collaborate, interact and share data to accomplish a task. A service invocation can involve multiple services, where each service generates, shares, and interacts with the client's data. These interactions may share data with unauthorized services and violate client's policies. The client has no means of identifying if a violation occurred and has no control or visibility on interactions beyond its trust domain. Such interactions introduce new security challenges which are not present in the traditional systems. We propose a data-centric approach for privacy preserving access control in SOA based on Active Bundles. This approach transforms passive data into an active entity that is able to protect itself. It enables dynamic data dissemination decisions and protects data throughout its lifecycle. The granularity of the data being shared with a service is determined by the client's data dissemination policy.
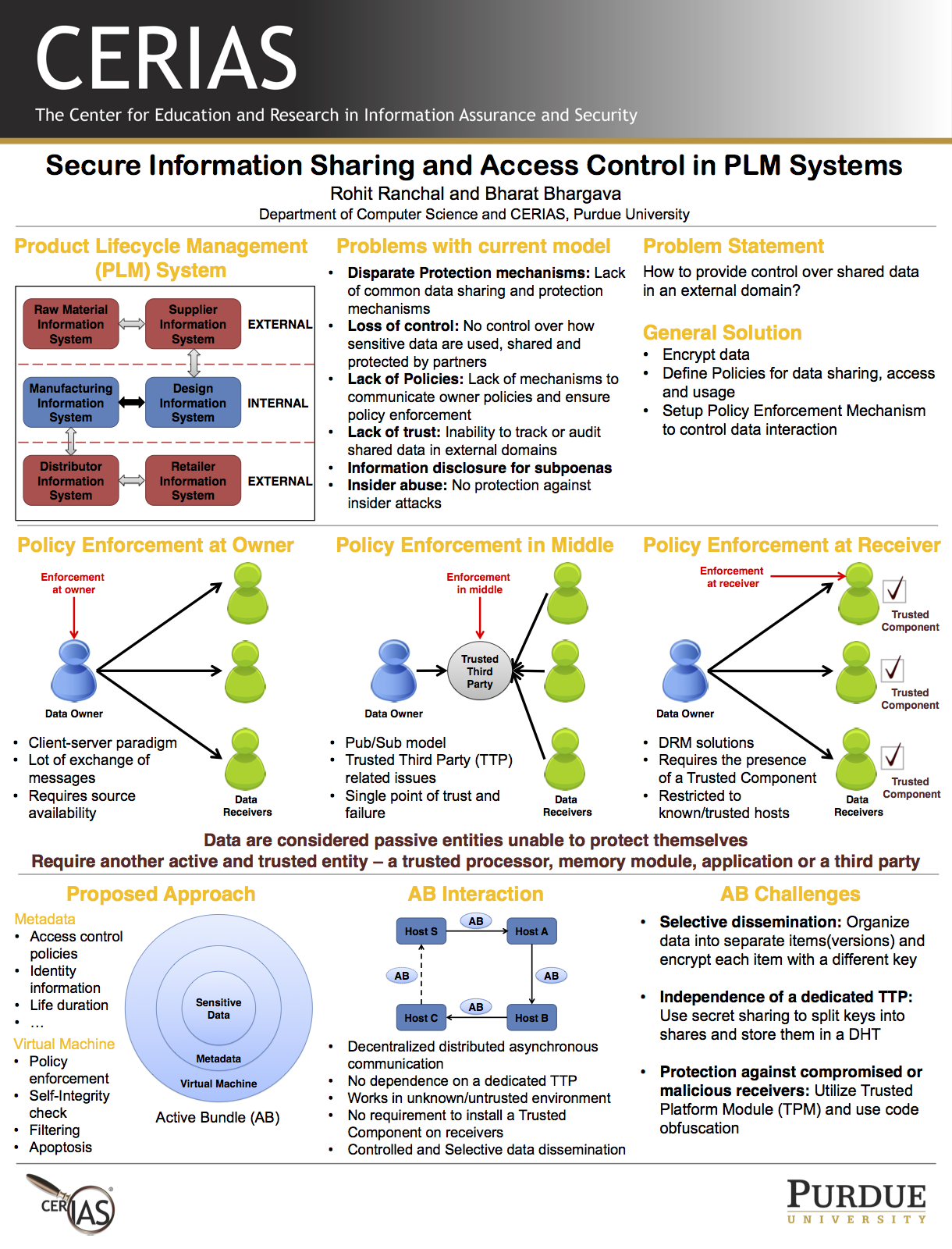
CERIAS Symposium 2013. Secure Information Sharing and Access Control in PLM Systems
Modern enterprises operate in a global economy with their operations dispersed across internal processes and external partners. A partner can be a sub-contractor to whom work is outsourced. Enterprises collaborate with their partners through Product Lifecycle Management (PLM) systems for producing and delivering products and services to consumers. Each partner in a PLM system uses data, generates data and shares data with other partners, and all this collaboration contributes to producing and delivering the products or services. Shared data may contain highly sensitive information such as trade secrets, intellectual property, private organizational or personal information. In large enterprise systems, it is difficult to understand and track data dissemination. The main security challenge in PLM is the unauthorized disclosure and data leakage of information shared among the partners. Existing approaches ensure security within the domain of an organization and don't address protection in a decentralized environment. We propose an approach for secure data dissemination using the Active Bundle scheme. This approach enables organizations to securely share information in their PLM steps and have control over its interaction in external domains.
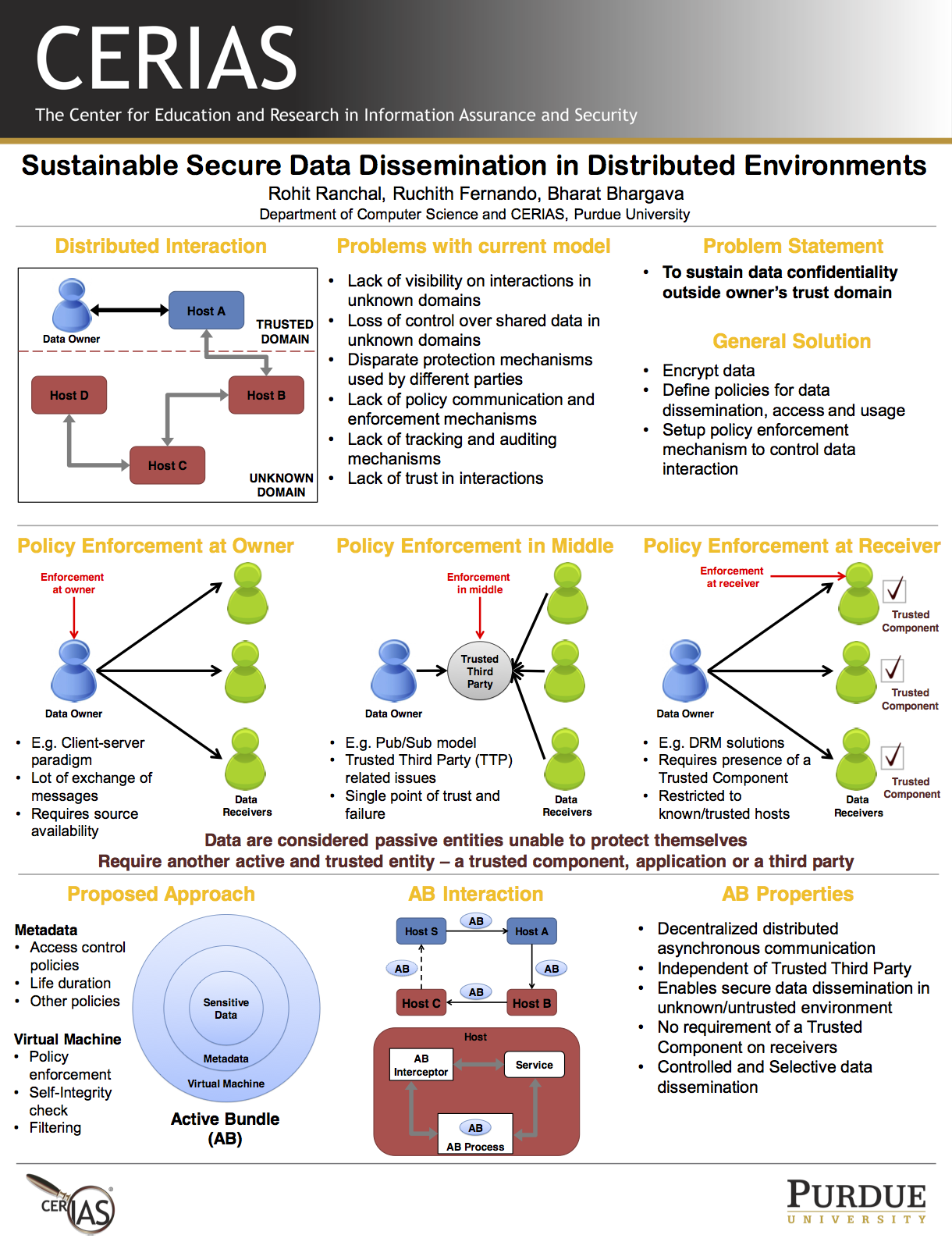
SustainIT Conference 2013. Sustainable Secure Data Dissemination in Distributed Environments
Modern distributed systems comprise of a number of loosely-coupled services, which collaborate, interact and share data to accomplish a task. This paradigm is currently used by many systems such as Service Oriented Architecture, Cloud Computing, Product Lifecycle Management, Pervasive Healthcare, Digital Supply Chains, Digital Rights Management, etc. An interaction can involve multiple parties, where each party generates, shares, uses and interacts with the data. Existing technologies for secure data sharing in point-to-point or client-server paradigms don't work in the distributed environment because of the involvement of multiple parties in an interaction. The main security challenge is that the data owner has no control and visibility on interactions beyond its trust domain, so it is difficult to understand and track data dissemination to unknown or untrusted parties. The interactions beyond the trust domain of data owner may share data to unauthorized parties and violate owner's policies and the owner has no way of knowing if a violation occurred. Such interactions introduce new security challenges not present in the traditional systems, where the focus is to ensure security within a single domain. Thus it is imperative to have a new solution that supports secure data dissemination in distributed interactions and protects data according to its owner's policies. In this poster, we describe a data-centric approach for end-to-end secure data dissemination. This approach transforms passive data into an active entity that is able to protect itself. It enables dynamic data dissemination decisions and protects data throughout its life cycle. The granularity of the data being shared with a party is determined by the respective dissemination policy of the data owner. This enables sustainability of data confidentiality outside the owner's trust domain.